Call of Duty’s Zombie Mod stands as an adrenaline-packed action and daunting challenge. This game mode puts players through a test of endurance. However, sometimes, the thrill of the game can morph into frustration as the difficulty spikes. It’s at times like these that a touch of ingenuity can alter the table’s turn. As a seasoned player and a passionate hacker, I believe in tilting the scales a bit towards our favor every once in a while.
This blog post will journey you through my unique exploration - a self-developed game hack specifically designed for the ‘Call of Duty Zombie Mod’. Consider it as a helping hand extended with love from one gamer to another, aiming to make those gaming sessions a little less daunting and a lot more enjoyable.
Hack content
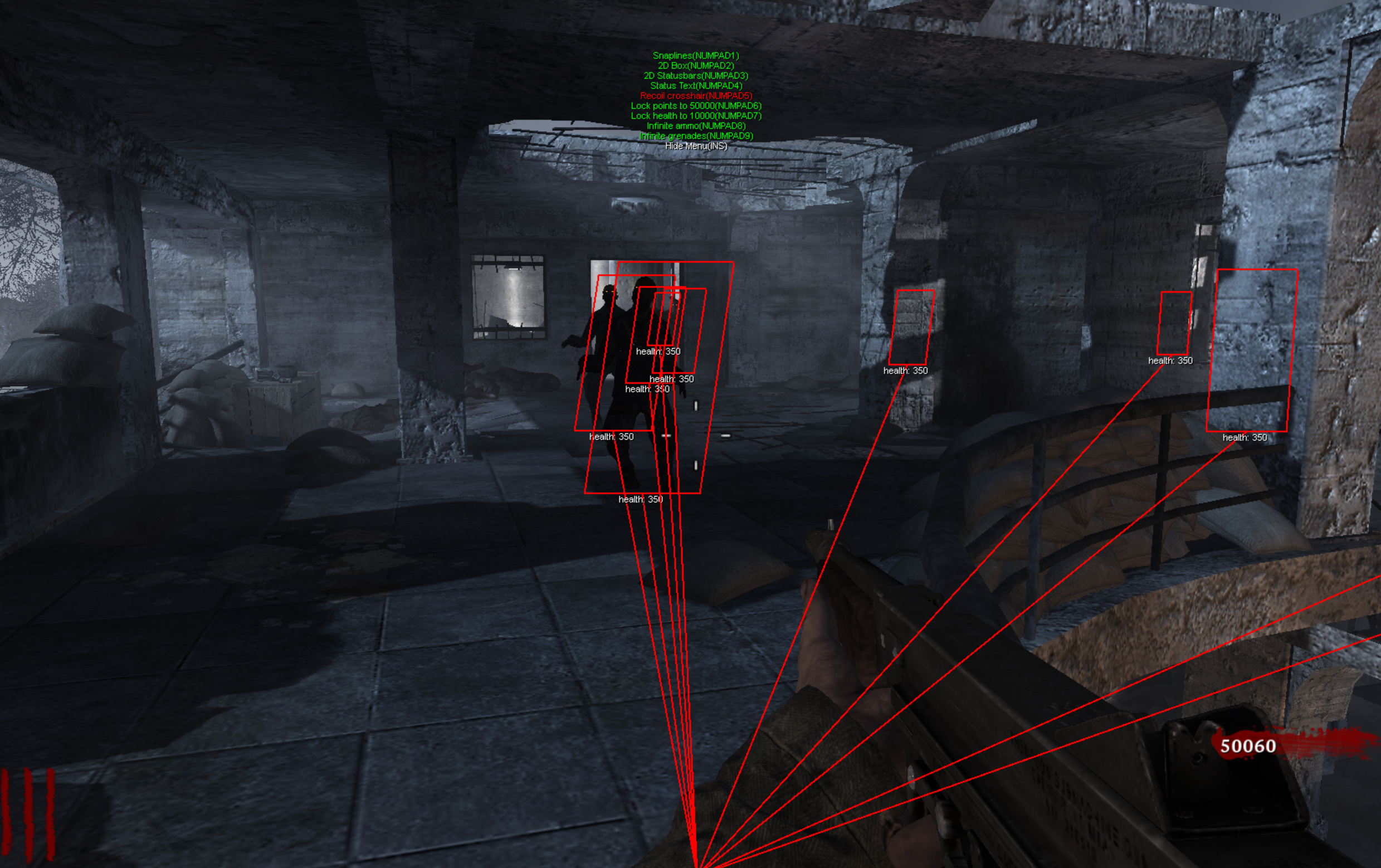
When you run hack a menu with hack options will show inside the game.
You can toggle the menu using Insert key on the keyboard.
The options inside the menu are:
Snaplines [Numpad 1]a red line will be drawn from local players view angle to zombie’s feet2D Box [Numpad 2]a red 2D box will be drawn around a zombie as a ESP feature so you can know where the zombies are (even behind walls)Status text [Numpad 4]a status text will appear beneath zombie with remaining health for specific zombieRecoil crosshair [Numpad 5]a custom crosshair will appear on the screen, since game one follows recoilLock points to 50000 [Numpad 6]a zombie points will constantly be set to 50000, therefore you can buy anything on the mapInfinite health [Numpad 7]Infinite ammo [Numpad 8]Infinite grenades [Numpad 9]Endto eject a dll
Source code: https://github.com/realbugdigger/Call-of-Duty-WaW-Hack
Overview of the hack execution
Hack is injected via dll injector. Next, when injected, it performs function hooking on Direct3D9 EndScene function. EndScene() is the function called when the game is finished drawing the next frame to be displayed on the screen, meaning all the drawing by the game is completed, so any drawing we do, will render on top of the finished scene. After our EndScene hook returns it will call the real EndScene and the image will be rendered on the screen. That makes hack execute every frame which makes it very fast!
In consideration of the comprehensive nature of this hack, delving into its entire depth would make for an extensive read. Therefore, this post will focus on explaining key components of the hack, ensuring a concise yet insightful information for the reader. This approach will provide a solid understanding of its prime features without overwhelming you with excessive detail.
Cheat table
Let’s start with cheat engine table that I set up.
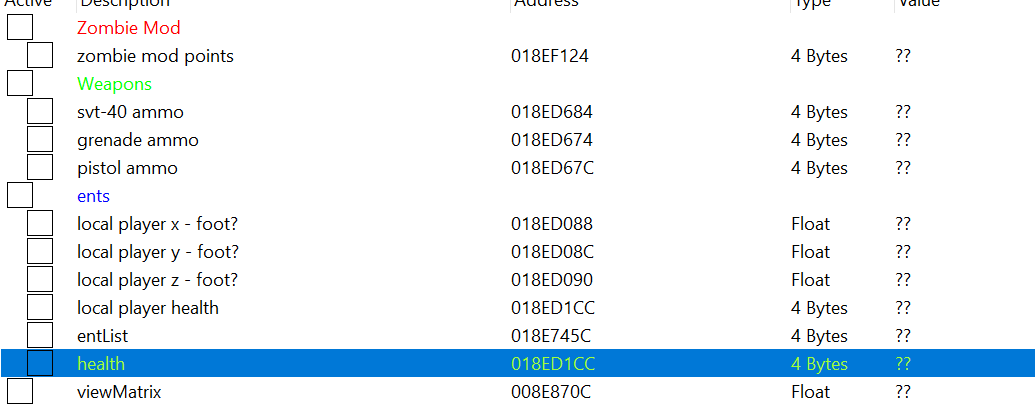
Zombie mod points and Grenades
Finding zombie mod points address was very easy. Entering starting value in cheat engine and increasing it each time zombie is killed and decreasing it whenever I would spend points.
By “Locking the value” what I am actually doing is writing the random value at the prevoisly found address every time hack executes.
Same thing was done with grenades, everytime I would throw it I would decrease the value in the cheat engine and when the address that contains the value was found I would overwrite it with custom value.
Infinite ammo
Same as for previous two values ammo value address was also found by decreasing and increasing (shooting and reloading). When I went to see what access it I saw an interesting instruction that was being executed no matter what weapon shot was selected. I thought that this must be part of some kind of “decrease ammo value” function!
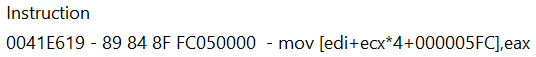
When nopping the instruction and shooting again, ammo was not decreasing.
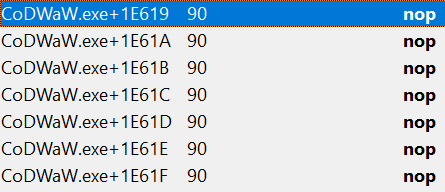
What is Nopping?
“Nopping” refers to the process of replacing an original instruction with a “No Operation” (NOP) command in assembly language. The NOP command is essentially an instruction that does nothing. “Nop” stands for “No Operation”. This process could be used for a number of purposes, including maintaining code alignment, adding delays, patching code, and others.
In the context of converting an original instruction into all NOP commands, it essentially means replacing functional instructions with instructions that do nothing, making the original code inert. These NOP commands still take up the same amount of memory as the instructions they’ve replaced, but when executed, they don’t change any registers, flags, or the program’s state. They just consume clock cycles.
Local player and Zombie data
Local player health and coordinates and for zombies was a bit harder to find. For player health I had to thrown grenades in near proximity so it would hurt me enough but not kill me, that moment was used to scan memory for a decreased value, and when player would start recovering, in cheat engine I would search for increased value. Similiar process was applied to zombies just without recovering.
When looking at the memory region where found address was located, in ReClass.Net I found local player coordinates and view angle.
For the cords of the zombies I decided to first find Z coordinate since will be easiest. I selected one random zombie a let him “follow me”. By that I mean whenever he followed my up the stairs I increased the unknown value of a Z coordinate for a zombie. And when he walked down I decreaded. Then when he was on “same level” as me on some platform I searched the value of my z coordinate since zombie will have the same. That’s how I found the z cord for one zombie. The x and y were right next to it.
I repeated the process for another zombie after I restarted the game and found out that two vector3 structures for those two zombies were relativly close in memory! I looked at that memory region in ReClass and started noticing some patterns, in the same memory region I found more cords for newly spawned zombies! As I did more reverse enginering I found some more data and metadata about the entity list I was looking at, but as I said I am trying to not make this blog post to long.
To conclude with entity list I found out that the size of the enities was 0x88. This will come in handy when writting ESP 2D boxes around zombies.
DLL injection
DLL Injection is a technique used for running code within the context of another process by forcing it to load a dynamic-link library (DLL). DLL injection is often used by external programs to influence the behavior of another program in a way its authors did not anticipate or intend.
Enumerating Processes
First step needed for Dll injection is to select which process we want to inject into. For the hack the name of executable is given codwaw.exe.
Windows system API function CreateToolhelp32Snapshot
will be used to take a snapshot of all processes running on the system at the moment.
We then need enumerate the running processes on the machine to see if any have the name of the process we want to inject into.
The injection steps
After getting process handle to the target process the next step is to inject the DLL into the target process which will require the use of several Windows APIs.
First the address of LoadLibraryW needs to be found. Why this function is used? It’s part of the kernel32.dll which is a dll that is loaded into every process running on the system.
The next step is to allocate memory in the remote process that can fit the DLL’s name using VirtualAllocEx.
After the memory is successfully allocated in the remote process, it’s possible to use WriteProcessMemory to write to the allocated buffer. The DLL’s name is written to the previously allocated memory buffer.
Finall step is using CreateRemoteThread
function will be used to create a new thread in the remote process.
This is where the address of LoadLibraryW becomes necessary. Address of LoadLibraryW will be starting address of the thread and then address of allocated buffer, which contains the DLL’s name, is passed as an argument to the LoadLibraryW call.
Both of these parameter are passed to CreateRemoteThread.
And voila the dll injection has happened.
Summary
As we draw this blog post to end, my hope is that this blog post has shed some valuable light on the fascinating realm of game hacks, in particular the practice of DLL injection. The intertwining complexities of gaming software and how we can navigate them has been our focus. The insights presented in this blog post aim to equip you with an understanding, and appreciation, of the multifaceted process that goes into creating a game hack. May this knowledge contribute to enhancing your passion for gaming and inspire you to explore more.